Table of Contents
Introduction
When we started looking for password managers for our DevOps team, Bitwarden Cloud was a natural first stop. It’s trusted, secure, and user-friendly — but it came with limitations that didn’t sit well with our priorities as a self-hosting, cost-conscious DevOps consultancy.
- We don’t do black boxes: While vault contents in Bitwarden are encrypted, metadata still lives on external servers. Things like item names, vault usage stats, and user behavior could still be visible to Bitwarden’s infrastructure. For teams handling client secrets or needing strict data residency, that’s a no-go.
- The features we need are paywalled: Essentials like TOTP generation, hardware key support (YubiKeys), and admin policies require a paid premium or enterprise plan. These features are vital for a DevOps team — not just “nice to have.”
- Self-hosting Bitwarden is possible — but heavy: Bitwarden’s official server stack requires multiple containers, MS SQL, and a .NET runtime. Worse, you still need to upload a license file to unlock admin policies or enforce 2FA. So while technically self-hosted, it still felt vendor-bound and operationally bloated.
In short: Bitwarden is excellent for many teams — but not lean or open enough for ours.
Why Vaultwarden Works for a DevOps Consultancy
Vaultwarden, the open-source Rust-based Bitwarden-compatible server, checked every box we care about — without locking features behind a license. Here’s why it clicked for us:
Security & Privacy
- Fully self-hosted: No user or vault data ever leaves our infrastructure
- Zero-trust server: Everything is end-to-end encrypted; the server just stores blobs
- Admin controls let us enforce strong master passwords and 2FA across the team
Cost
- No per-user fees, no subscriptions, no catch
- Enterprise-grade features like TOTP, WebAuthn, and vault policies are free
- Easy to scale across projects and environments without thinking about licenses
Customizability
- Invite-only signups and user management from an admin dashboard
- Works out of the box with all Bitwarden clients (mobile, desktop, browser)
- CLI and API access make it scriptable — ideal for secrets in CI/CD pipelines
Performance & Simplicity
- One Rust-based binary/server — tiny memory footprint, minimal CPU usage
- Docker and Helm support make deployment effortless
- No MS SQL bloat, no complex orchestration — just one pod and you're done
For a DevOps agency that’s comfortable managing its own infra, Vaultwarden offers freedom without complexity.
How We Host It Internally
We run Vaultwarden in a dedicated Kubernetes namespace using the community Helm chart from Guerzon's repository. Our deployment is streamlined yet robust:
Deployment Architecture
huzaif@airflow-1:~/do-helmfile/vaultwarden$ kubectl get all -n vaultwarden
+ kubectl get all -n vaultwarden
NAME READY STATUS RESTARTS AGE
pod/vaultwarden-c59f5f95f-vdrpt 1/1 Running 0 7d1h
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/vaultwarden ClusterIP 10.245.75.148 <none> 80/TCP 57d
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/vaultwarden 1/1 1 1 57d
NAME DESIRED CURRENT READY AGE
replicaset.apps/vaultwarden-5495879964 0 0 0 57d
replicaset.apps/vaultwarden-594d49445 0 0 0 57d
replicaset.apps/vaultwarden-678cf6949 0 0 0 57d
replicaset.apps/vaultwarden-76787b8ffd 0 0 0 57d
replicaset.apps/vaultwarden-85dbc5864c 0 0 0 57d
replicaset.apps/vaultwarden-c59f5f95f 1 1 1 55dThe output shows our simple but effective setup - a single replica deployment with a ClusterIP service that's been running reliably for months.
Configuration Management
We use helmfile for declarative configuration management
- PostgreSQL database backend for reliable data storage
- Environment variables loaded via a simple bash script
- Resource limits set to keep resource usage predictable (200m CPU, 256Mi memory)
- Organization creation restricted to admin emails only
- Domain-restricted signups (kubenine.com only)
Secure External Access
Unlike typical ingress-based setups, we expose Vaultwarden using Cloudflare Tunnels:
- No public Kubernetes endpoints or open firewall ports
- Zero trust architecture with Cloudflare acting as the identity provider
- DDoS protection through Cloudflare's edge network
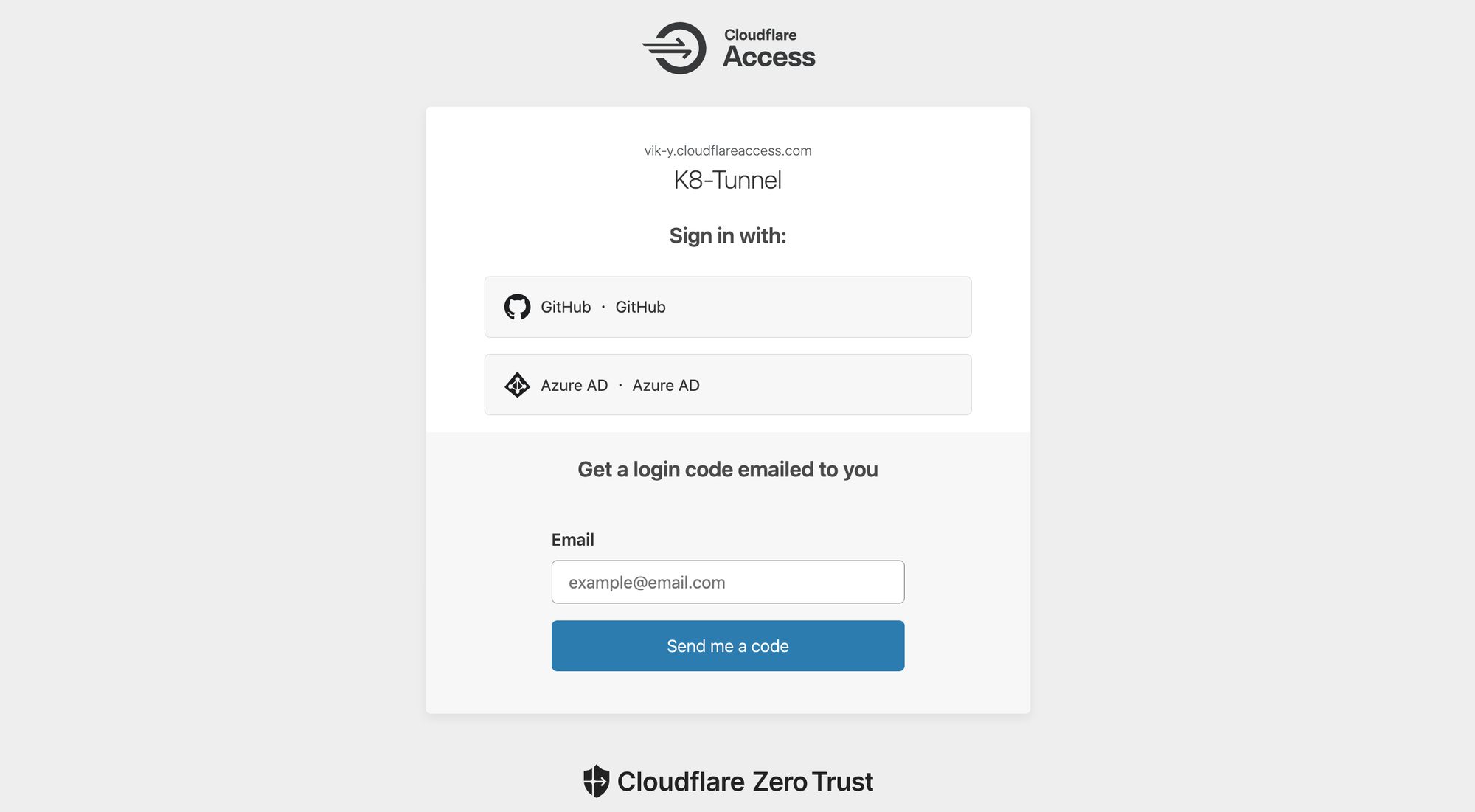
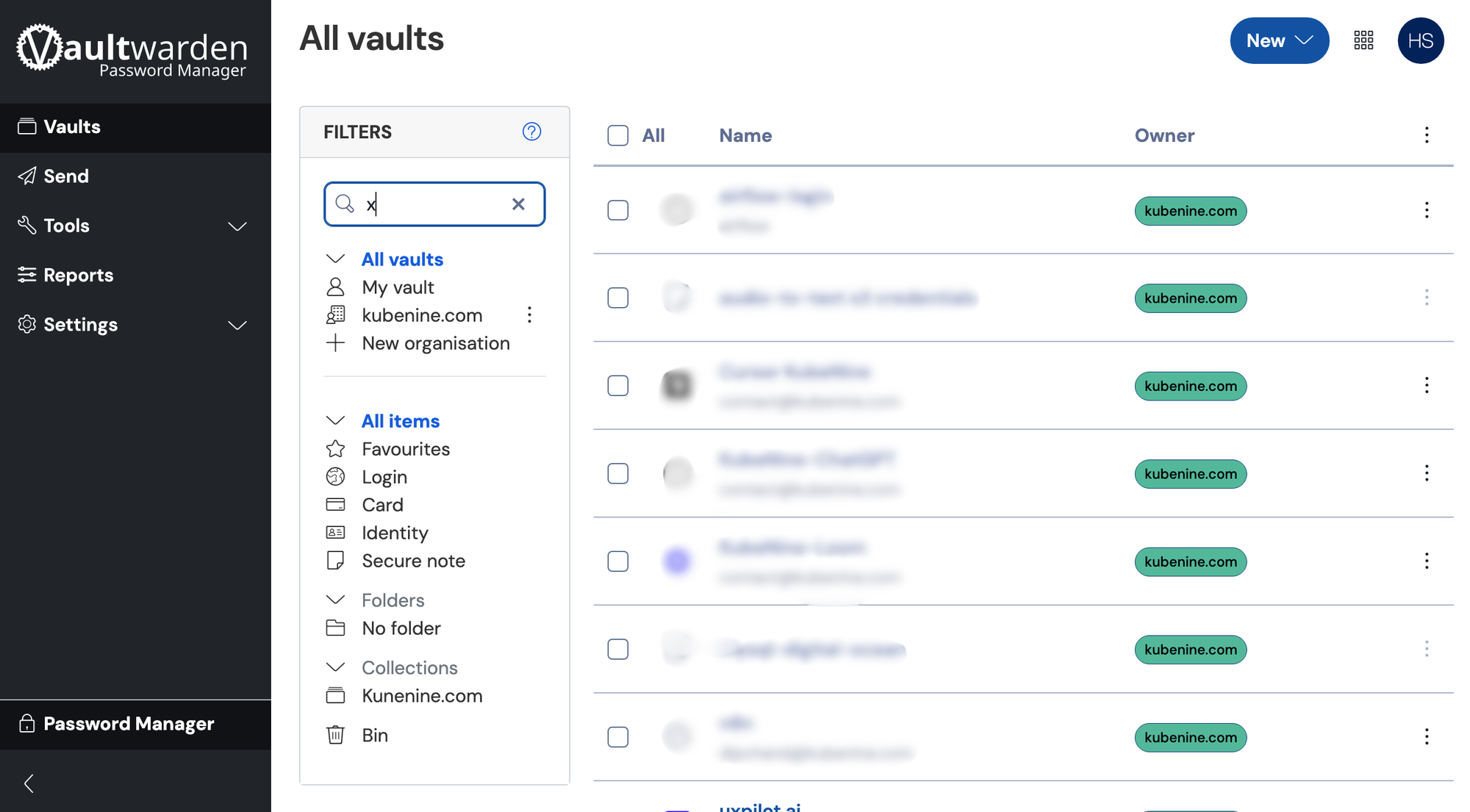
It's lightweight enough that we barely notice it's running — and it just works.
Conclusion
Vaultwarden gave us everything we wanted in a password manager — without vendor lock-in, per-user billing, or external dependencies. It aligns with how we think DevOps should operate: secure by design, infra under control, minimal overhead.
Would like to get this configured for your organisation? KubeNine can help, reach out to us!