Table of Contents
Introduction
Google Cloud Platform (GCP) and Amazon Web Services (AWS) both offer VPCs, but they handle network scope, connectivity, and scaling in different ways. It’s important to know these differences when you’re building apps on these platforms.
You might have heard often - “I know AWS - I can quickly adapt to GCP - it’s fundamentally same”. Well it’s a myth - while both are cloud platforms, they vary on a lot of critical things like IAM, Networking and more.
In this post, we’ll compare AWS’s regional VPC with GCP’s global VPC, and we’ll also look at how peering and gateways work on both platforms. By the end, you’ll have a clear idea of the main differences and which one might work best for you.
What is a VPC?
A Virtual Private Cloud (VPC) is like a private network in the cloud, giving you the power to control:
- Subnet placement (private or public access)
- Firewall rules (which traffic is allowed in or out)
- Routing (where traffic flows and how)
In simpler terms, it’s your own data center running on a provider’s infrastructure. Each cloud provider has the concept of regions. A region is a grouping of one or more data centers.
Spreading workloads across multiple regions provides high availability by duplicating services across those regions. We can also place resources closer to customers.
The way networking utilizes the regions is similar between Azure and AWS — and different with GCP.
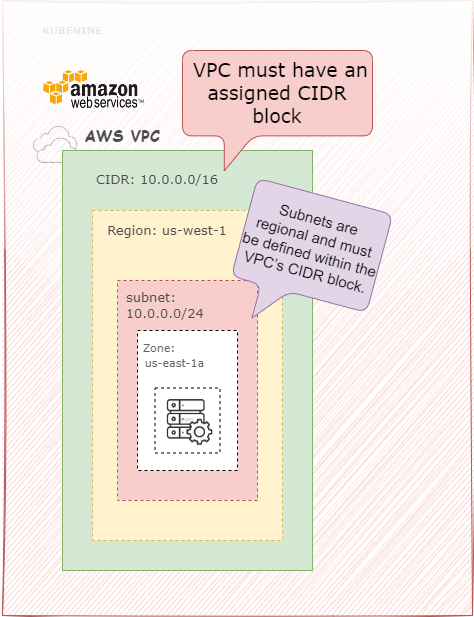
AWS VPC – Regional Networking
How AWS VPC Works
AWS uses a regional VPC model. When you create a VPC in AWS, it’s tied to one region, and it cannot span multiple regions. This means:
- If you have deployments in us-east-1, us-west-1, and eu-west-1, you must create three separate VPCs.
- Each VPC has its own CIDR block (for example, 10.0.0.0/16 in us-east-1, 10.1.0.0/16 in us-west-1, 10.2.0.0/16 in eu-west-1).
- Cross-region communication requires VPC Peering or an AWS Transit Gateway.
Example: AWS Multi-Region Setup
Region | VPC Name | CIDR Block |
|---|---|---|
us-east-1 | vpc-prod-us | 10.0.0.0/16 |
us-west-1 | vpc-prod-west | 10.1.0.0/16 |
eu-west-1 | vpc-prod-eu | 10.2.0.0/16 |
Key Characteristics of AWS VPC
- One VPC per region
- Subnets belong to Availability Zones within that region
- Manual setup required for cross-region routing
- Security groups and NACLs (network ACLs) are managed on a per-VPC basis
Limitations of AWS’s Regional Model
- Scaling to new regions requires creating a new VPC and repeating network configuration.
- Overlapping CIDRs can prevent direct VPC Peering.
- Inter-region traffic is billed per GB, increasing costs for global apps.
- Security rules must be duplicated in each region.
Despite these challenges, AWS VPC is popular for fine-grained control and region-specific isolation, which can be useful for certain compliance needs.
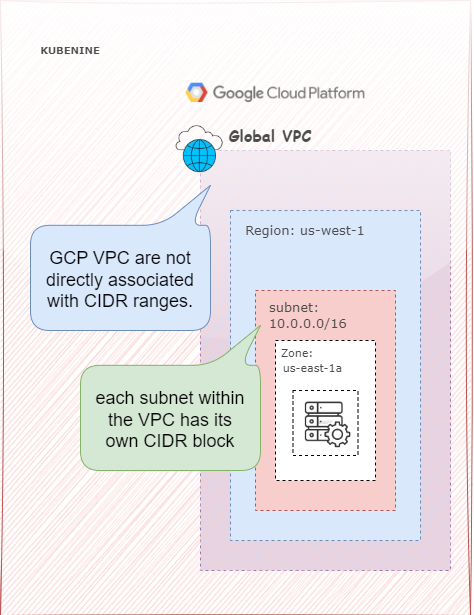
GCP VPC – Global Networking
How GCP VPC Works
In contrast, GCP offers a global VPC, meaning a single VPC can exist across multiple regions. You do not need to create a brand-new VPC for each region. Instead, you create subnets in different regions, all within one global VPC.
Example: GCP Multi-Region Setup
Subnet Name | Region | CIDR Block | VPC Name |
|---|---|---|---|
subnet-prod-us | us-central1 | 10.10.0.0/24 | prod-vpc |
subnet-prod-eu | europe-west1 | 10.10.1.0/24 | prod-vpc |
subnet-prod-asia | asia-east1 | 10.10.2.0/24 | prod-vpc |
Key Characteristics of GCP VPC
- One VPC can span multiple regions
- Subnets are assigned their own CIDR blocks within the same VPC
- Cross-region communication happens natively within Google’s backbone
- Lower inter-region transfer costs compared to AWS
Benefits of GCP’s Global Model
- Easier Multi-Region Scaling – Add a subnet in a new region without creating a new VPC.
- No Overlapping CIDR Issues within the same VPC.
- No additional configuration needed for inter-region connectivity.
- Single set of firewall rules and IAM-based policies across regions.
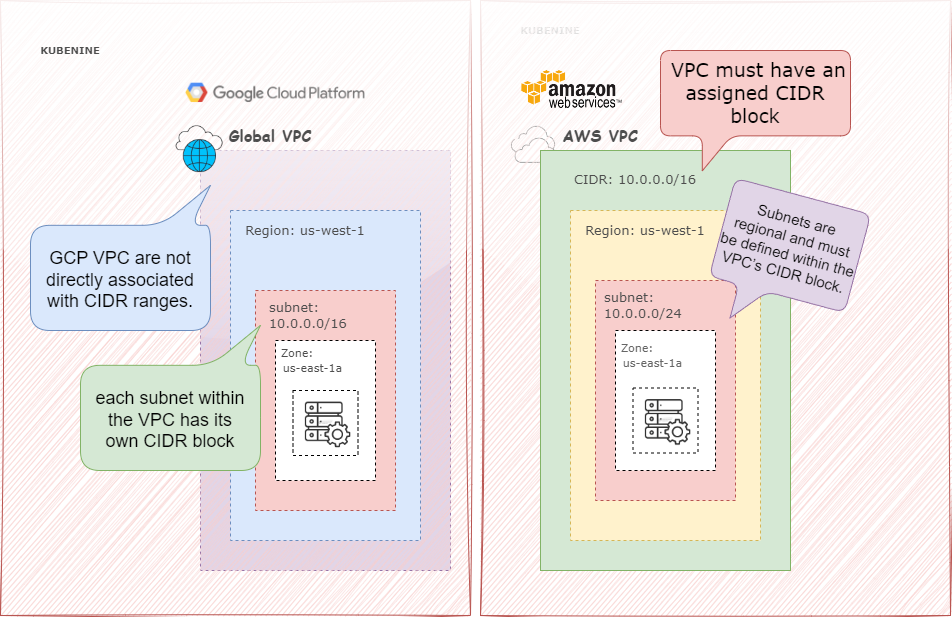
AWS vs. GCP: Key Differences in VPC Design
Feature | AWS VPC (Regional) | GCP VPC (Global) |
|---|---|---|
VPC Scope | One VPC per region | One VPC spans multiple regions |
CIDR Block Scope | Assigned per VPC | Assigned per subnet |
Cross-Region Communication | Requires Peering or Transit Gateway | Native within the same VPC |
Scaling | New VPC for each region | Add subnets in existing global VPC |
Data Transfer Costs | Higher inter-region fees | Lower inter-region costs via Google’s backbone |
Security Management | Security groups & NACLs per region | IAM-based firewall rules across the global VPC |
High Availability | Must deploy multiple VPCs in different regions | Can be done within one global VPC |
Hybrid Connectivity | Uses Direct Connect, VPN Gateway | Uses Cloud Interconnect, Cloud VPN |
Peering Complexity | Manual peering needed between VPCs, not transitive | VPC Peering is not transitive across different projects |
Connecting Multiple Networks – Peering and Gateways
So far, we’ve covered VPCs and subnets in AWS and GCP. Let’s address how to connect these networks so applications can communicate across different VPCs or even across different projects.
Peering (AWS and GCP)
Both AWS and GCP support VPC Peering to connect two separate VPCs. However, peering is not transitive on both platforms. If Network A is peered with Network B, and Network B is peered with Network C, then A and C cannot communicate unless you create an additional peering between A and C.
Challenges with Peering
- Maintenance overhead grows with more networks.
- Overlapping CIDR ranges break peering.
- Hard to scale for large organizations with many VPCs or projects.
Gateways (AWS and GCP)
To avoid the complexity of building a large “mesh” of peering connections, both AWS and GCP offer gateway solutions that act as a hub-and-spoke model.
AWS Gateways
- AWS Transit Gateway
- Connects multiple VPCs within or across regions.
- Acts as a central router where each VPC only needs one attachment to the Transit Gateway.
- Scales well for enterprises with many VPCs.
- AWS VPN Gateway (Virtual Private Gateway)
- Creates encrypted tunnels from on-premises networks to AWS over public internet.
- AWS Direct Connect Gateway
- Dedicated link for on-prem connectivity.
- Works with AWS Direct Connect for more predictable network performance.
GCP Gateways
- Shared VPC
- Multiple GCP projects can share a single VPC, avoiding the need for peering.
- All subnets and services operate under one main VPC managed by a central team.
- Cloud VPN
- Encrypted tunnel over the public internet from on-premises to GCP.
- Cloud Interconnect
- Private, dedicated link between on-premises and GCP.
- Similar to AWS Direct Connect, offers better bandwidth and less latency.
Peering vs. Gateways in Real-World Use
1. Hub-and-Spoke with Transit Gateway (AWS)
A global financial firm might use AWS Transit Gateway to connect:
- VPC A (Trading platform)
- VPC B (Analytics)
- VPC C (Archiving)
Instead of three separate peering connections, each VPC attaches to the Transit Gateway. That gateway then routes traffic between them as needed.
2. Multi-Project GCP Setup with Shared VPC
A SaaS startup runs multiple services across separate GCP projects:
- Project A (Frontend APIs)
- Project B (Data Processing)
- Project C (Machine Learning)
They create one Shared VPC in Project A and let B and C use subnets from that Shared VPC. No additional peering connections are required for internal communication.
3. Hybrid Connectivity
Whether it’s AWS or GCP, connecting on-premises data centers typically involves:
- A VPN for quick setup over the public internet (slower, but flexible).
- A dedicated interconnect or direct connect for better performance and lower latency (requires a third-party network provider to physically link the data center to the cloud region).
Conclusion
Both AWS VPC and GCP VPC offer strong networking foundations, but they take different paths. AWS focuses on region-based isolation, requiring more setup for multi-region deployments. GCP embraces a global VPC model, making cross-region networking simpler by default.
When your architecture involves multiple networks, projects, or on-premises connectivity, peering alone may become a bottleneck. Gateways (like AWS Transit Gateway or GCP Shared VPC) deliver a hub-and-spoke design that simplifies large-scale networking.
If you still have questions about which VPC model fits your use case, or how to integrate gateways and peering in the most efficient way, feel free to reach out to KubeNine (or your chosen cloud consulting partner). The right strategy depends on scale, compliance needs, and workload distribution—and having expert guidance can save significant time and cost.






