Table of Contents
Introduction
Cloud security auditing is critical but often tedious and time-consuming. AWS CloudTrail logs every API call and user activity, offering a detailed audit trail. But combing through these logs manually or writing complex CloudWatch Insights queries is a painful and error-prone task.
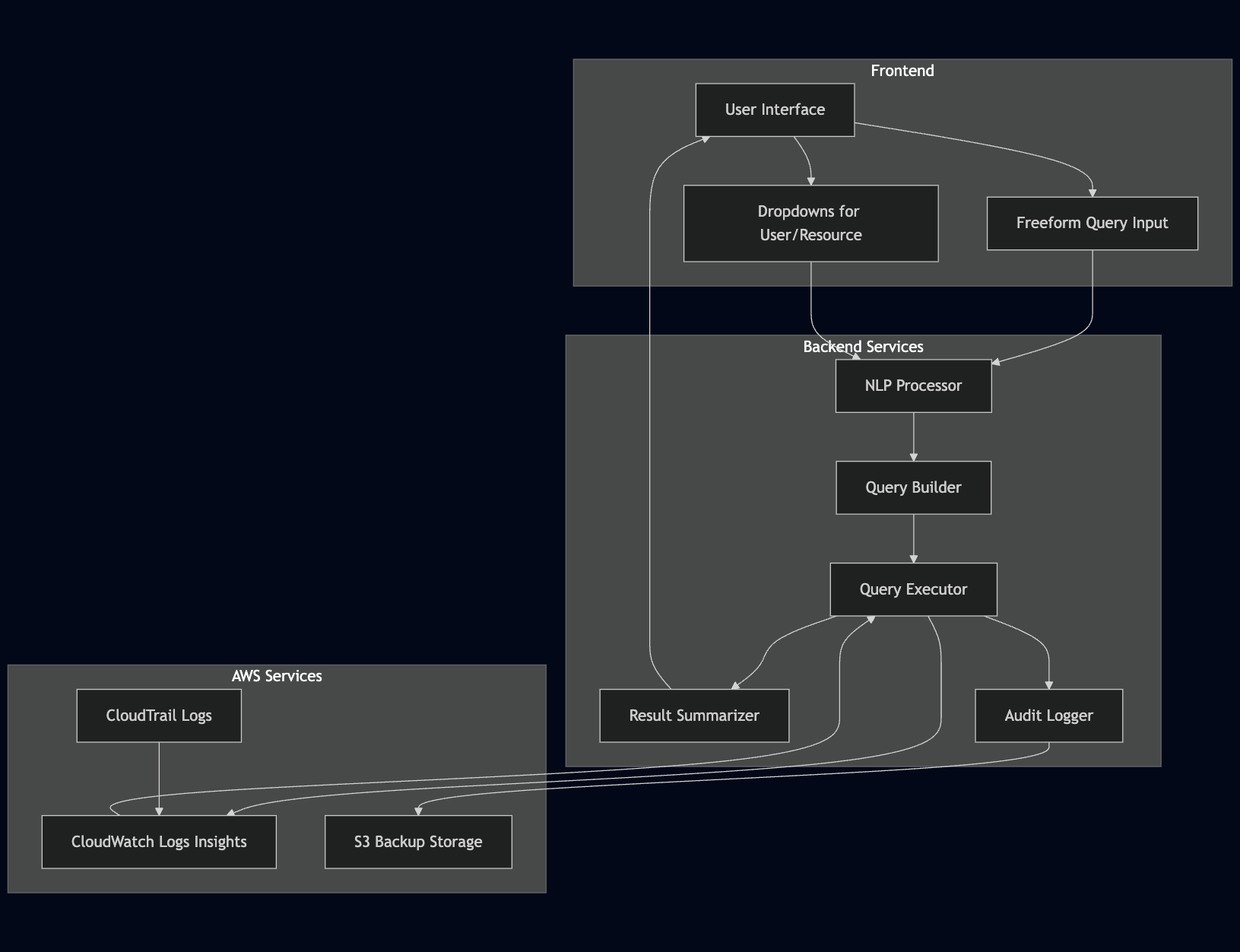
We at KubeNine have built an AI-powered CloudTrail analyzer that transforms the way teams interact with logs. What if you could just ask your logs a question like: “Which IAM users created new roles last week?” Or select a username from a dropdown and instantly get a summary of their activities? No more going through JSON or creating CLI queries, just ask, click, and know.
Why Traditional Methods Weren’t Enough
The traditional log analysis typically involves:
- Navigating CloudWatch Logs.
- Crafting complex queries in CloudWatch Logs Insights.
- Filtering data manually to spot critical events.
- Writing scripts to fetch activity across services or users.
These methods are often slow as it can take a lot of time to go from a security question to a clear answer and is often not accessible for non-technical team members as they can’t write or understand these complex queries.
We saw an opportunity to remove this friction and make CloudTrail data more understandable and actionable.
Project Goals
Our goal wasn’t just to reduce friction, it was to ease the process of auditing data and making it so that everyone in the team understood what’s really going on.
Our solution:
- Eliminates the need to write CloudWatch queries manually.
- Allows security and DevOps teams to interact with logs using plain English.
- Provide contextual summaries per IAM user, SSO user, and AWS resource.
- Maintain a lightweight, serverless footprint using only native AWS tools.
Technical Challenges & Solutions
Challenge 1: Natural Language Understanding
We needed a system that could understand questions like “List all EC2 instances launched yesterday” or “What actions did SSO user John perform last week?”
Solution: We integrated OpenAI’s GPT-4.1 model to interpret natural language queries and map them to relevant CloudWatch Logs Insights syntax. A smart prompt engineering layer helps GPT extract the intent, time range, and relevant fields to generate the right query even for complex or multi-service questions.
Challenge 2: AWS Integration
Executing queries, fetching logs, and correlating them across services like IAM, EC2, and S3 required robust AWS SDK usage.
Solution: We used Boto3 to interface with CloudWatch Logs, retrieving data based on GPT-generated queries. We also built fallback mechanisms to ensure we could gracefully handle empty or ambiguous responses.
Challenge 3: Result Presentation
Raw logs are hard to read. Even after getting the query right, the output isn’t very helpful unless it’s translated into insights.
Solution: We built a GPT-powered summarization engine that converts the results of each query into readable summaries. This turns complex JSON logs into statements like:
- “IAM user JohnDoe created a new role and attached admin privileges.”
- “SSO user Jane accessed the billing console from a new device.”
This makes reports easy to digest — even for stakeholders outside the engineering team.
Feature Highlights
We didn’t stop at just natural language queries. We built additional features that make this tool a necessity for cloud security and compliance teams:
- IAM User Summary: Get a timeline of activities for any IAM user — logins, key creation, policy changes, and more.
- SSO User Summary: See what federated or SSO users did in your account — role assumptions, console logins, resource access.
- Per-Resource Summary: Understand the lifecycle of any AWS resource — from creation to deletion, with all user interactions in between.
- Sensitive Activity Reports: Ask questions like “Who created access keys?” or “Was MFA disabled?” and get a quick answer.
User Impact
With this app, our users now:
- Spend 90% less time writing queries.
- Empower non-technical team members to perform audits.
- Detect suspicious behavior faster.
- Generate audit reports instantly, without sifting through raw logs.
And perhaps most importantly, they gain visibility across all actions in their AWS environment in a way that’s simple, secure, and scalable.
Conclusion
The CloudTrail Query Application started as a side project to simplify our own log investigations but quickly evolved into a powerful internal product. It represents the next step in how cloud-native teams manage security, compliance, and visibility.
By combining GPT’s language capabilities with AWS’s raw power, we’ve turned tedious log analysis into a seamless, conversational experience. And we’re just getting started.
You can try it out at: https://github.com/kubenine/cloudtrail-tool
If you're tired of wrestling with CloudWatch queries, get in touch with us at KubeNine — and let us show you what’s possible when logs start speaking your language.