Table of Contents
Managing secrets in Kubernetes can be a real headache. If you've ever struggled with keeping environment variables secure and up-to-date across multiple clusters, I totally get it. Many of us have faced the hassle of manual secret management, and it's time we found a better way.
I often used to think how much easier things would be if I could manage secrets via the web browser or an API and I finally found something which does exactly that.
In this blog post, I'll introduce you to Doppler, a tool that makes secret management in Kubernetes so much easier. We'll walk through how to implement the Doppler Kubernetes Operator using Helm, step by step. By the end, you'll know what Doppler is, how it works, and how it can help you.
The Challenges of Secret Management in Kubernetes
Kubernetes is a powerful platform, but dealing with secrets can be tough:
- Manual Processes: Updating secrets by hand takes a lot of time and can lead to mistakes. When you're managing multiple files and environments, it's easy to mess up.
- Security Risks: If secrets aren't stored properly, sensitive information can leak. This can cause compliance issues and security breaches.
- Scalability Issues: As your applications grow, keeping secrets consistent across environments gets more complicated.
These problems can slow down your development process and put your data at risk. But there's a solution.
Introducing Doppler
Doppler is a secret management platform designed to simplify how you handle environment variables and secrets. Here's what it offers:
- Centralized Secret Storage: Keep all your secrets in one secure place.
- Environment Variable Management: Easily manage variables across development, staging, and production.
- Team Collaboration Tools: Work smoothly with your team, with proper access controls.
- Version Control and Audit Logs: Track changes and maintain compliance without hassle.
By integrating Doppler with Kubernetes, you can automate secret management, reduce errors, and improve security.
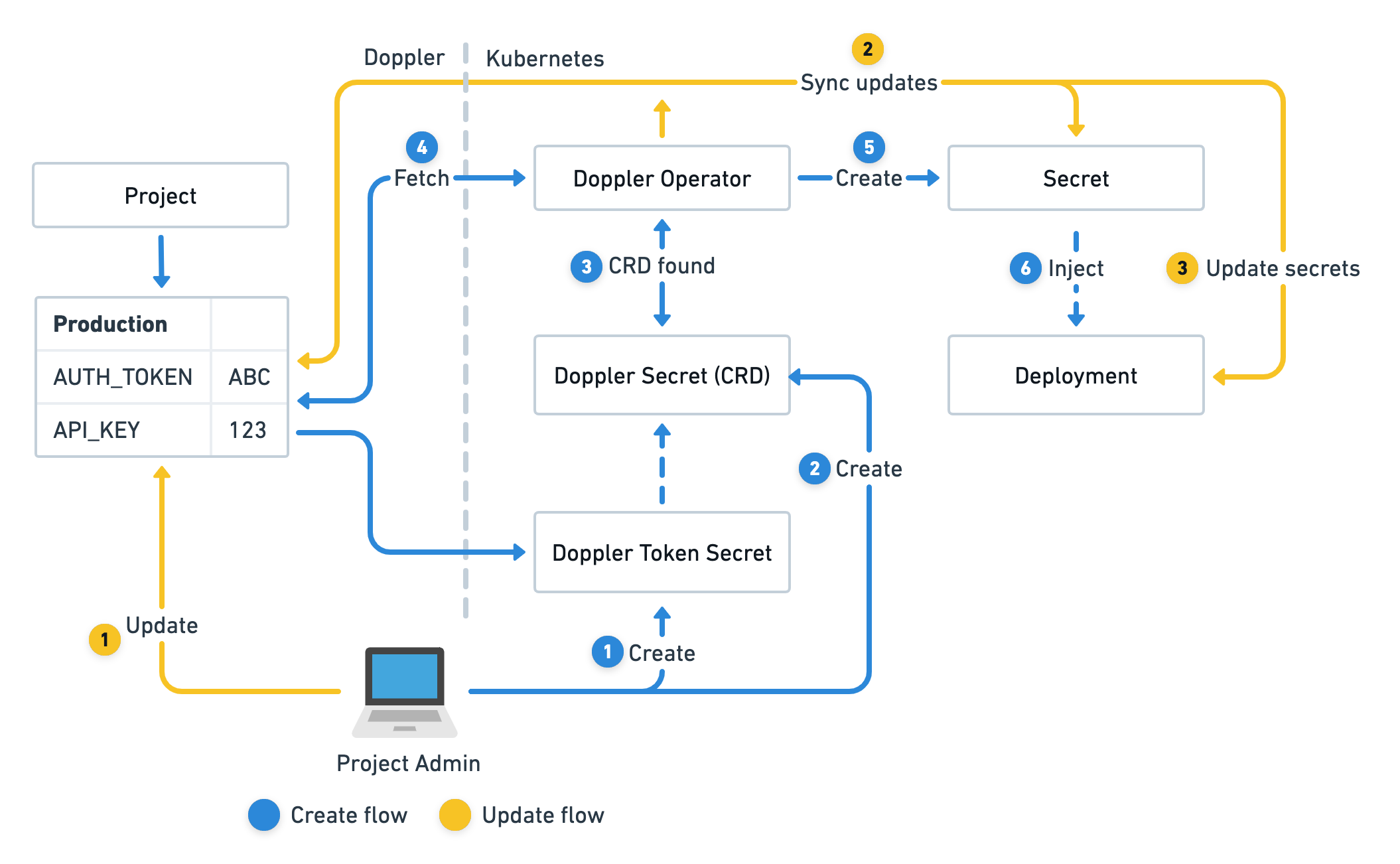
How Does the Doppler Kubernetes Operator Work?
Before we jump into the setup, let's understand how the Doppler Kubernetes Operator works in your cluster.
In Kubernetes, an Operator is like an assistant that helps manage applications and resources. It uses custom resources and controllers to automate tasks that would otherwise need manual work.
The Doppler Kubernetes Operator connects your Doppler secrets to your Kubernetes cluster. Here's how it works:
- Custom Resource Definition (CRD): The operator introduces a new resource type called
DopplerSecret. You use this to tell Kubernetes which Doppler project and configuration to sync. - Continuous Syncing: Once you create a
DopplerSecret, the operator keeps an eye on your Doppler project. If there are any changes to the secrets, it updates them in Kubernetes automatically. - Automated Updates: The operator updates your Kubernetes secrets whenever something changes in Doppler. This means your applications always have the latest secret values without you having to do anything.
- Secure Connection: The operator uses a service token (stored securely in Kubernetes) to access your Doppler account. This keeps the connection between Doppler and your cluster safe.
By using the operator, you don't have to update secrets manually anymore. It reduces the risk of errors and makes sure all your environments stay in sync.
Step-by-Step Guide to Implementing Doppler Kubernetes Operator Using Helm
Let's get started with setting up Doppler in your Kubernetes cluster using Helm.
Prerequisites
Before we begin, make sure you have the following:
- A running Kubernetes cluster
- Kubernetes command-line tool (
kubectl) configured - Helm package manager installed
- A Doppler account with necessary permissions
Step 1: Install the Doppler Kubernetes Operator Using Helm
First, we'll install the Doppler Kubernetes Operator using Helm.
Add the Doppler Helm Repository:
helm repo add doppler https://helm.doppler.com
Update Helm Repositories:
helm repo update
Install the Operator:
helm install doppler-operator doppler/doppler-operator
This command installs the operator into your Kubernetes cluster.
Step 2: Create a Doppler Service Token
We need to give the operator access to your Doppler secrets.
Generate a Service Token:
- Log in to your Doppler account through your web browser.
- Navigate to your project.
- Go to Settings > Service Tokens.
- Click on Create Service Token.
- Give your token a name and select the appropriate scopes.
- Click Create and copy the generated token. We'll need it in the next step.
Step 3: Configure Access to Doppler Projects
Now, we'll securely provide the service token to the operator.
Create a Kubernetes Secret for the Doppler Token:
Replace YOUR_DOPPLER_SERVICE_TOKEN with the token you copied earlier.
kubectl create secret generic doppler-token --from-literal=serviceToken=YOUR_DOPPLER_SERVICE_TOKEN
Step 4: Define Secrets to Sync
We'll tell the operator which secrets to sync.
Create a DopplerSecret Custom Resource:
Create a file named dopplersecret.yaml with the following content:
apiVersion: secrets.doppler.com/v1alpha1
kind: DopplerSecret
metadata:
name: my-doppler-secret
spec:
project: your-doppler-project
config: dev
secretName: doppler-secrets
serviceTokenSecret:
name: doppler-token
key: serviceToken- Replace
your-doppler-projectwith your actual project name in Doppler. - Replace
devwith the configuration you want to use (e.g., staging, production).
Apply the Configuration:
kubectl apply -f dopplersecret.yaml
Step 5: Update Your Kubernetes Deployments
Now, we'll update your application to use the synced secrets.
Create a Complete Deployment File:
Create a file named deployment.yaml with the following content:
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
spec:
replicas: 1
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:latest
ports:
- containerPort: 80
envFrom:
- secretRef:
name: doppler-secretsThis deployment uses the nginx image and pulls in environment variables from the doppler-secrets secret.
Step 6: Verify the Implementation
Let's make sure everything is working.
Check Synced Secrets:
kubectl get secrets kubectl describe secret doppler-secrets
These commands show that the secrets are present and contain the expected data.
Test the Application:
You can port-forward to the nginx service to test it locally:
kubectl port-forward deployment/nginx-deployment 8080:80
Visit http://localhost:8080 in your browser to see the nginx welcome page. While nginx doesn't use environment variables by default, this setup ensures your application has access to the secrets if needed.
Frequently Asked Questions (FAQs)
- Can I use Doppler with multiple Kubernetes clusters?
Yes, you can use Doppler with multiple Kubernetes clusters. You just need to install the Doppler Kubernetes Operator on each cluster and configure them with the appropriate service tokens and DopplerSecret resources.
- How does Doppler handle secret rotation?
Doppler automatically syncs any changes to your secrets, including rotations. When you update a secret in Doppler, the operator updates the Kubernetes secret, and your applications will receive the new values.
- Is it safe to store the Doppler service token in a Kubernetes secret?
Yes, storing the service token in a Kubernetes secret is secure, as long as you follow best practices for securing your cluster. Make sure to restrict access to secrets and use role-based access control (RBAC) to limit who can view them.
- What happens if the Doppler service is temporarily unavailable?
If Doppler is temporarily unavailable, the operator will retry syncing the secrets until the service is back online. Your existing secrets in Kubernetes will remain unchanged, so your applications should continue running without interruption.
Conclusion
Managing secrets in Kubernetes doesn't have to be a headache. With Doppler and Helm, you can automate the process, improve security, and save time.
We've walked through setting up Doppler in your Kubernetes cluster, from installing the operator to deploying your application with a complete deployment file. By following these steps, you'll have a reliable secret management system that's easy to maintain.
If you haven't tried Doppler yet, I encourage you to give it a shot. It might just make your life a whole lot easier.
Checkout our article on all the new features in Kubernetes 1.30 at: https://www.kubeblogs.com/explore-all-the-new-features-in-kubernetes-1-30/






