Table of Contents
Introduction
Enterprise data protection requirements have become increasingly complex, with regulations like GDPR, HIPAA, SOX, and industry-specific standards mandating specific backup retention periods and recovery capabilities. Managing daily, weekly, and monthly backups across multiple databases, storage systems, and applications manually becomes an operational nightmare that introduces compliance risks and potential data loss.
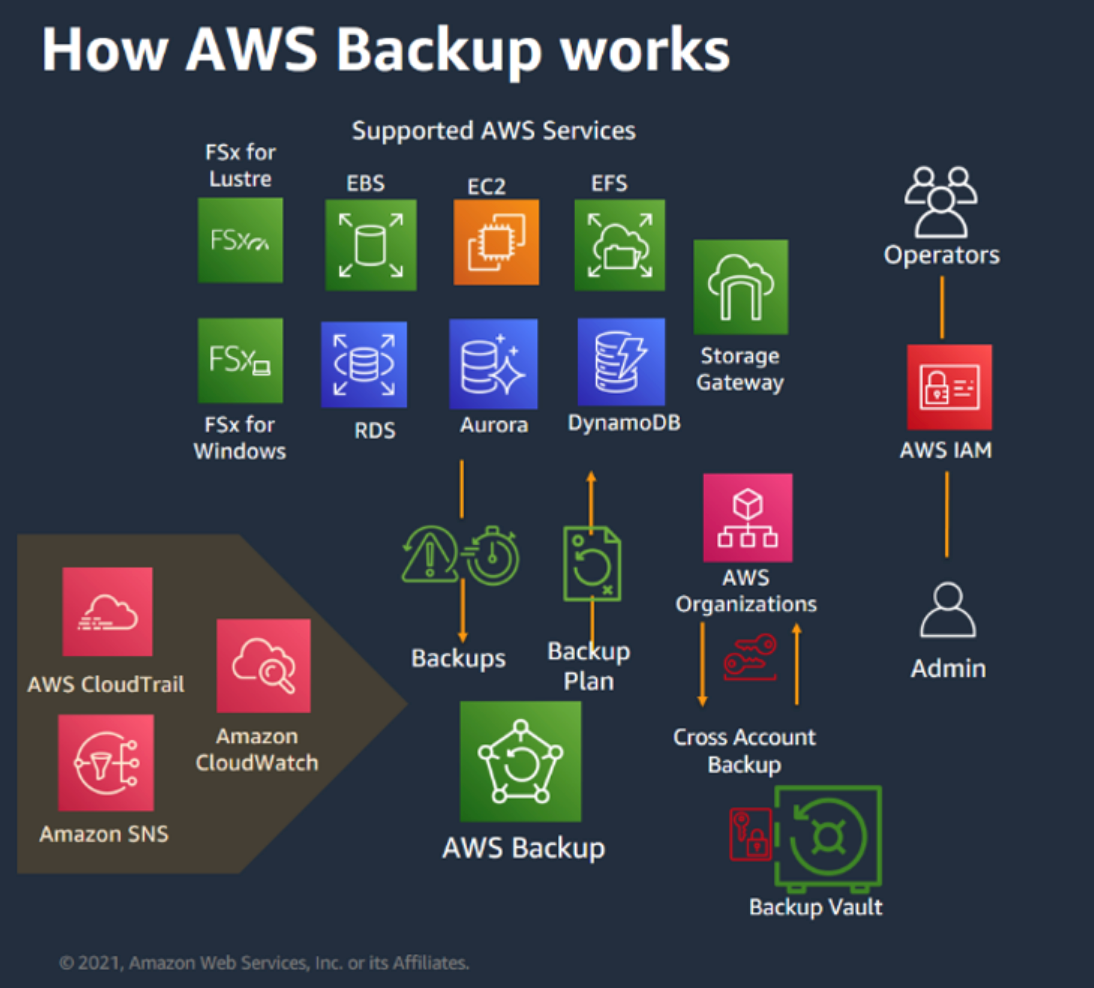
AWS Backup provides a centralized, policy-driven approach to data protection that eliminates the complexity of managing individual backup solutions. Instead of configuring backup policies for each resource separately, organizations can create comprehensive backup plans with automated retention rules, cross-region copies, and compliance reporting. This service integrates with many AWS services, including RDS, DynamoDB, EBS, EFS, and EC2, providing a unified backup strategy that meets enterprise compliance requirements.
This AWS Backup compliance guide demonstrates how to implement enterprise-grade data protection policies, covering backup plan creation, resource assignment, retention policies, and monitoring. We'll explore how to design backup strategies that satisfy regulatory requirements while maintaining operational efficiency and cloud security standards.
At KubeNine Consulting, we specialize in helping organizations implement comprehensive AWS Backup compliance strategies. Our team of experienced DevOps engineers and cloud architects has successfully designed and deployed enterprise backup solutions that meet GDPR, HIPAA, SOX, and other regulatory requirements across various industries.
Understanding AWS Backup Architecture
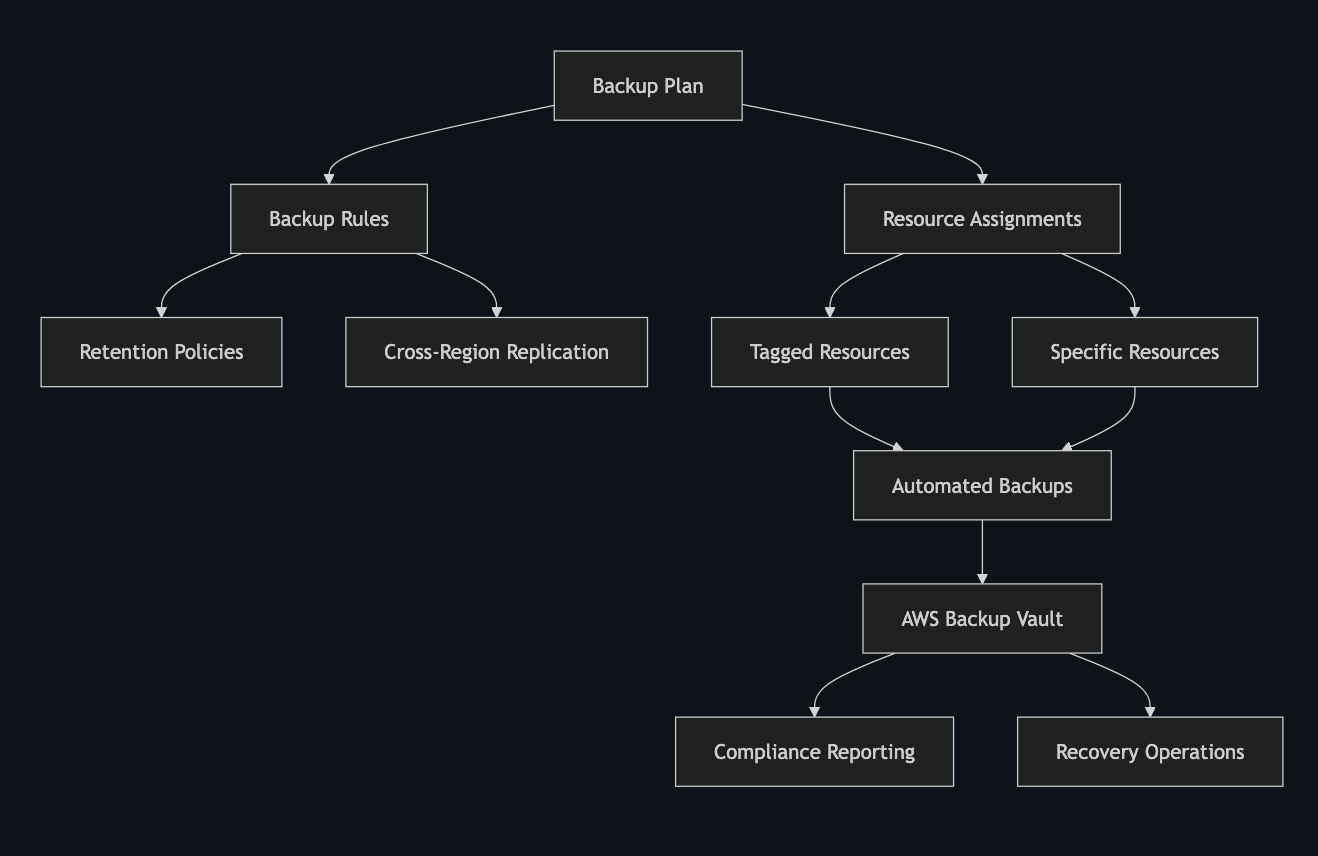
AWS Backup operates through three core components: backup plans, backup rules, and selections (resource assignments). This keeps the setup generic and scalable: define once, and apply broadly across your entire AWS infrastructure.
The AWS Backup service provides a centralized backup management solution that simplifies compliance monitoring and ensures consistent data protection policies across all your cloud resources. This architecture enables organizations to maintain regulatory compliance while reducing operational complexity and backup management overhead.
Step-by-Step Implementation
Understanding AWS Backup Architecture
AWS Backup operates through three core components: backup plans, backup rules, and selections (resource assignments). This keeps the setup generic and scalable: define once, apply broadly.
Step 1: Create a Backup Vault
Start by creating a dedicated backup vault to store your compliance backups. This vault will contain all backup data and can be configured with encryption and access controls.
Option: Enable AWS Backup Vault Lock (WORM) for immutability and to enforce retention.
# Create a backup vault with encryption
aws backup create-backup-vault \
--backup-vault-name "compliance-backup-vault" \
--encryption-key-arn "arn:aws:kms:us-east-1:123456789012:key/abcd1234-5678-90ef-ghij-klmnopqrstuv" \
--tags Key=Environment,Value=Production Key=Compliance,Value=SOXStep 2: Define Backup Rules for Compliance
Create backup rules that define frequency and retention. A typical enterprise backup strategy includes daily, weekly, and monthly retention periods. Optionally, you can add cross-Region and cross-account copy actions to these rules.
{
"BackupRules": [
{
"RuleName": "DailyBackupRule",
"TargetBackupVault": "compliance-backup-vault",
"ScheduleExpression": "cron(0 2 * * ? *)",
"StartWindowMinutes": 60,
"CompletionWindowMinutes": 120,
"Lifecycle": {
"DeleteAfterDays": 30
}
},
{
"RuleName": "WeeklyBackupRule",
"TargetBackupVault": "compliance-backup-vault",
"ScheduleExpression": "cron(0 3 ? * SUN *)",
"StartWindowMinutes": 60,
"CompletionWindowMinutes": 120,
"Lifecycle": {
"DeleteAfterDays": 90
}
},
{
"RuleName": "MonthlyBackupRule",
"TargetBackupVault": "compliance-backup-vault",
"ScheduleExpression": "cron(0 4 1 * ? *)",
"StartWindowMinutes": 60,
"CompletionWindowMinutes": 120,
"Lifecycle": {
"DeleteAfterDays": 2555
},
"CopyActions": [
{
"DestinationBackupVaultArn": "arn:aws:backup:us-west-2:123456789012:backup-vault:compliance-backup-vault-dr",
"Lifecycle": { "DeleteAfterDays": 2555 }
}
]
}
]
}Step 3: Create the Backup Plan
Combine your backup rules into a comprehensive backup plan that will be applied to your resources.
# Create backup plan with compliance rules
aws backup create-backup-plan \
--backup-plan file://compliance-backup-plan.jsonThe backup plan JSON structure:
{
"BackupPlanName": "EnterpriseComplianceBackup",
"Rules": [
{
"RuleName": "DailyBackupRule",
"TargetBackupVault": "compliance-backup-vault",
"ScheduleExpression": "cron(0 2 * * ? *)",
"StartWindowMinutes": 60,
"CompletionWindowMinutes": 120,
"Lifecycle": {
"DeleteAfterDays": 30
}
},
{
"RuleName": "WeeklyBackupRule",
"TargetBackupVault": "compliance-backup-vault",
"ScheduleExpression": "cron(0 3 ? * SUN *)",
"StartWindowMinutes": 60,
"CompletionWindowMinutes": 120,
"Lifecycle": {
"DeleteAfterDays": 90
}
},
{
"RuleName": "MonthlyBackupRule",
"TargetBackupVault": "compliance-backup-vault",
"ScheduleExpression": "cron(0 4 1 * ? *)",
"StartWindowMinutes": 60,
"CompletionWindowMinutes": 120,
"Lifecycle": {
"DeleteAfterDays": 2555
}
}
]
}Step 4: Assign Resources to Backup Plan
Use selections to automatically include resources in your backup plan. You can assign resources by tags, by specific ARNs, or (optionally) by service-level wildcard ARNs.
Method 1: Tag-Based Resource Assignment
Create a selection that automatically includes all resources with specific tags:
aws backup create-backup-selection \
--backup-plan-id <backup-plan-id> \
--backup-selection '{
"SelectionName": "prod-tag-selection",
"IamRoleArn": "arn:aws:iam::123456789012:role/AWSBackupDefaultServiceRole",
"ListOfTags": [
{"ConditionType":"STRINGEQUALS","ConditionKey":"BackupEnabled","ConditionValue":"true"},
{"ConditionType":"STRINGEQUALS","ConditionKey":"Environment","ConditionValue":"Production"}
]
}'Method 2: Specific Resource Assignment
For critical resources, assign them directly to ensure they're always included:
aws backup create-backup-selection \
--backup-plan-id <backup-plan-id> \
--backup-selection '{
"SelectionName": "critical-rds-db",
"IamRoleArn": "arn:aws:iam::123456789012:role/AWSBackupDefaultServiceRole",
"Resources": [
"arn:aws:rds:us-east-1:123456789012:db:production-database"
]
}'Option: Service-level selection (e.g., all RDS)
Where appropriate, you can target an entire service using wildcard ARNs so new resources are covered automatically (validate in your account and Region):
aws backup create-backup-selection \
--backup-plan-id <backup-plan-id> \
--backup-selection '{
"SelectionName": "all-rds",
"IamRoleArn": "arn:aws:iam::123456789012:role/AWSBackupDefaultServiceRole",
"Resources": [
"arn:aws:rds:us-east-1:123456789012:db:*"
]
}'Step 5: Cross-Region and Cross-Account Copies (Option)
If you have business continuity or compliance requirements to store backups in another Region/account, add CopyActions to your backup rules. This automatically creates copies in a destination vault.
{
"RuleName": "MonthlyBackupRule",
"TargetBackupVault": "compliance-backup-vault",
"ScheduleExpression": "cron(0 4 1 * ? *)",
"Lifecycle": { "DeleteAfterDays": 2555 },
"CopyActions": [
{
"DestinationBackupVaultArn": "arn:aws:backup:us-west-2:123456789012:backup-vault:compliance-backup-vault-dr",
"Lifecycle": { "DeleteAfterDays": 2555 }
}
]
}Notes:
- Cross-account copies require a destination vault in the target account and appropriate IAM/backup vault access policies in that account.
- You can also manage copies and selections centrally with AWS Organizations backup policies (option).
Step 6: Monitor and Validate Compliance
Implement monitoring and alerting to ensure your backup compliance policies are working correctly.
# Check backup job status
aws backup list-backup-jobs \
--by-resource-type RDS \
--by-state COMPLETED
# Monitor backup vault metrics
aws backup get-backup-vault-access-policy \
--backup-vault-name "compliance-backup-vault"
# List backup selections
aws backup list-backup-selections \
--backup-plan-id "backup-plan-id"Option: Use AWS Backup Audit Manager to define controls and generate daily compliance reports, and (optionally) feed findings into AWS Audit Manager.
Step 7: Implement Compliance Reporting
Create automated compliance reporting using AWS Backup APIs and CloudWatch metrics.
import boto3
import json
from datetime import datetime, timedelta
def generate_compliance_report():
backup_client = boto3.client('backup')
# Get backup plan details
backup_plans = backup_client.list_backup_plans()
compliance_report = {
'report_date': datetime.now().isoformat(),
'backup_plans': [],
'compliance_status': 'COMPLIANT'
}
for plan in backup_plans['BackupPlans']:
plan_details = backup_client.get_backup_plan(BackupPlanId=plan['BackupPlanId'])
# Check if retention policies meet compliance requirements
for rule in plan_details['BackupPlan']['Rules']:
if 'Lifecycle' in rule and 'DeleteAfterDays' in rule['Lifecycle']:
retention_days = rule['Lifecycle']['DeleteAfterDays']
# SOX compliance requires 7 years (2555 days)
if rule['RuleName'] == 'MonthlyBackupRule' and retention_days < 2555:
compliance_report['compliance_status'] = 'NON_COMPLIANT'
compliance_report['violations'] = [
f"Monthly backup retention ({retention_days} days) below SOX requirement (2555 days)"
]
return compliance_report
# Generate and store compliance report
report = generate_compliance_report()
print(json.dumps(report, indent=2))Compliance Framework Integration
SOX Compliance Requirements
For SOX compliance, ensure your backup policies include:
- 7-year retention for financial data backups
- Daily backups for critical systems
- Cross-region replication for disaster recovery
- Encryption at rest and in transit
- Access logging and audit trails
GDPR Compliance Considerations
GDPR compliance requires:
- Right to be forgotten - implement backup deletion policies
- Data portability - ensure backups can be exported
- Encryption - protect personal data in backups
- Access controls - limit who can access backup data
HIPAA Compliance for Healthcare
Healthcare organizations need:
- Encrypted backups with customer-managed keys
- Access logging for all backup operations
- Retention policies that align with medical record requirements
- Audit trails for compliance reporting
Best Practices for Enterprise Implementation
1. Start with a Pilot Program
Begin with non-critical resources to validate your backup policies before applying them to production systems.
2. Use Tag-Based Resource Management
Implement consistent tagging strategies to automatically include new resources in your backup policies.
3. Test Recovery Procedures Regularly
Schedule monthly recovery tests to ensure your backup compliance policies actually work when needed.
4. Monitor Backup Success Rates
Set up CloudWatch alarms for backup failures to maintain compliance posture.
5. Document Everything
Maintain detailed documentation of your backup policies for audit purposes.
Cost Optimization Strategies
1. Use Intelligent Tiering
Configure backup lifecycle policies to move older backups to cheaper storage tiers.
2. Implement Cross-Region Replication Selectively
Only replicate critical backups to avoid unnecessary costs.
3. Monitor Backup Storage Usage
Regularly review and clean up unnecessary backups to control costs.
Conclusion
AWS Backup provides a powerful, centralized solution for implementing compliance-ready data protection policies across your entire AWS infrastructure. By creating comprehensive backup plans with automated retention policies, cross-region replication, and resource assignments, organizations can eliminate the complexity of managing individual backup solutions while ensuring regulatory compliance.
The key to success lies in designing backup policies that align with your specific compliance requirements, implementing proper resource tagging strategies, and maintaining ongoing monitoring and validation. With AWS Backup, you can transform your data protection strategy from a manual, error-prone process into an automated, compliant, and reliable system.
For organizations struggling with complex backup compliance requirements, AWS Backup offers a path to simplified, automated data protection that meets enterprise standards while reducing operational overhead.
Need help implementing AWS Backup for your compliance requirements? KubeNine Consulting specializes in designing and implementing enterprise-grade backup strategies that meet regulatory standards. Our team of experienced DevOps consultants can help you create comprehensive backup policies, implement automated compliance monitoring, and ensure your data protection strategy meets all regulatory requirements. Contact us at http://kubenine.com to learn how we can help strengthen your backup compliance posture.