How to Enhance Cloud Security Audits with Prowler: Step-by-Step Guide

Introduction
I bumped across Prowler (https://github.com/prowler-cloud/prowler) when my team was looking for a tool using which we could write custom checks to ensure security of our account.
Prowler is an open-source security tool designed to help you assess, audit, and improve the security of your AWS, Azure, Google Cloud, and Kubernetes environments. Think of it as your security advisor that ensures your cloud setup is following best practices and staying secure.
Architecture
Prowler can be run from various platforms, whether it's from your workstation, a Kubernetes Job, a Google Compute Engine, an Azure VM, or an EC2 instance. It's flexible and can fit into many different environments. The tool includes two main components: the Prowler CLI (Command Line Interface) and Prowler SaaS.
- Prowler CLI: This is the core tool you run from the command line. You can use it to perform security checks, generate reports, and more.
- Prowler SaaS: This is a service built on top of the CLI, providing additional features and a user-friendly dashboard for managing your security assessments.
Solution
Imagine you’re managing a company’s cloud infrastructure. You’ve got servers, databases, and services spread across AWS, Azure, Google Cloud, and Kubernetes. Keeping track of security best practices can be overwhelming. This is where Prowler steps in.
You can run Prowler to perform a thorough security assessment of your cloud environments. It checks your setup against a wide range of security standards like CIS, NIST, GDPR, and more. With hundreds of checks available, Prowler ensures that your infrastructure meets industry standards and highlights any potential security gaps.
Here’s how it works:
- Install Prowler: You can easily install Prowler using pip or Docker. For instance, you can run
pip install prowlerif you're using Python. - Run Security Checks: Use the Prowler CLI to start assessments. For example,
prowler awswill check your AWS setup, whileprowler azuredoes the same for Azure. - View Results: After running the checks, Prowler provides detailed reports. You can review these reports to see if any issues need addressing.
Common Prowler Commands
- Run a Full Security Check for AWS:
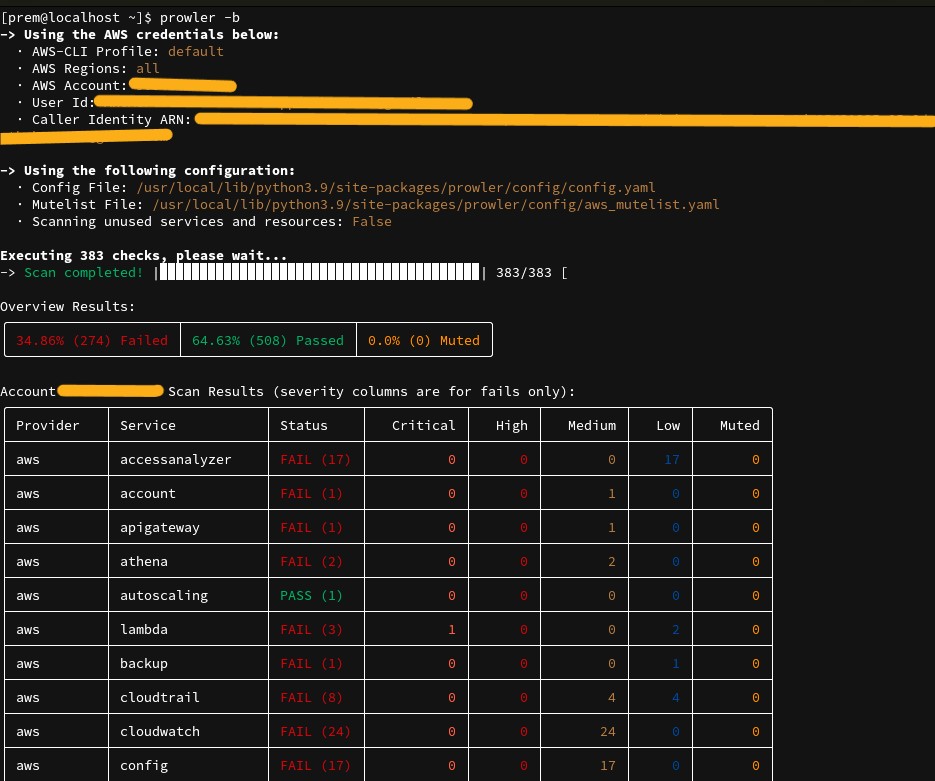
prowler -b
Explanation: This command runs all available checks for your AWS environment. The -b flag (bulk mode) ensures that it covers all aspects, from general best practices to specific compliance checks like CIS and GDPR.
- Run a Check for a Specific AWS Service:
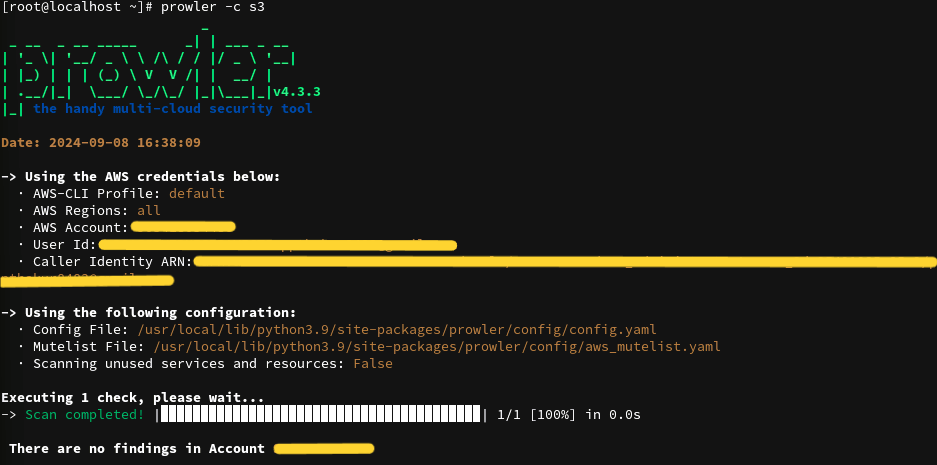
prowler -c s3
Explanation: If you want to run checks related to a specific AWS service, such as S3, EC2, or IAM, you can use the -c flag . This helps you focus on a particular area rather than checking everything.
- Generate Reports in Multiple Formats:
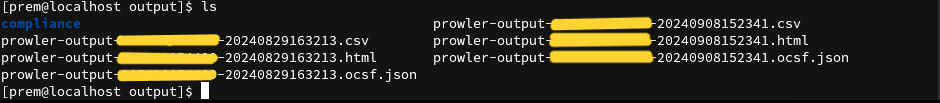
prowler -M csv,json,html
Explanation: This command generates the security check results in multiple formats like CSV, JSON, and HTML. It's useful for sharing the reports with team members or for integrating the results into other systems.
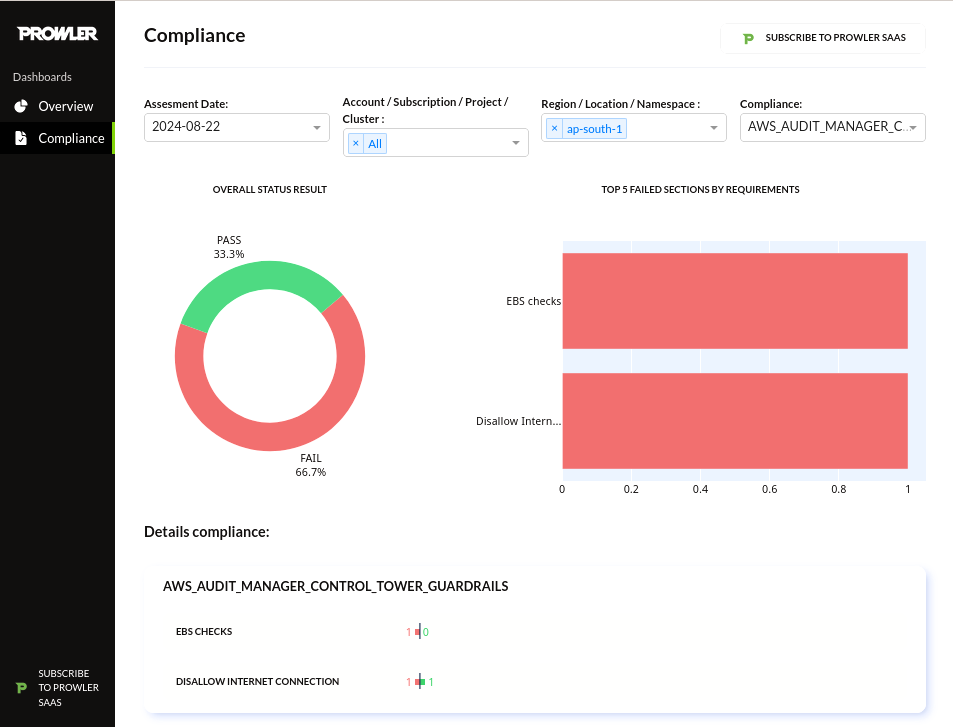
- Prowler Dashboard:
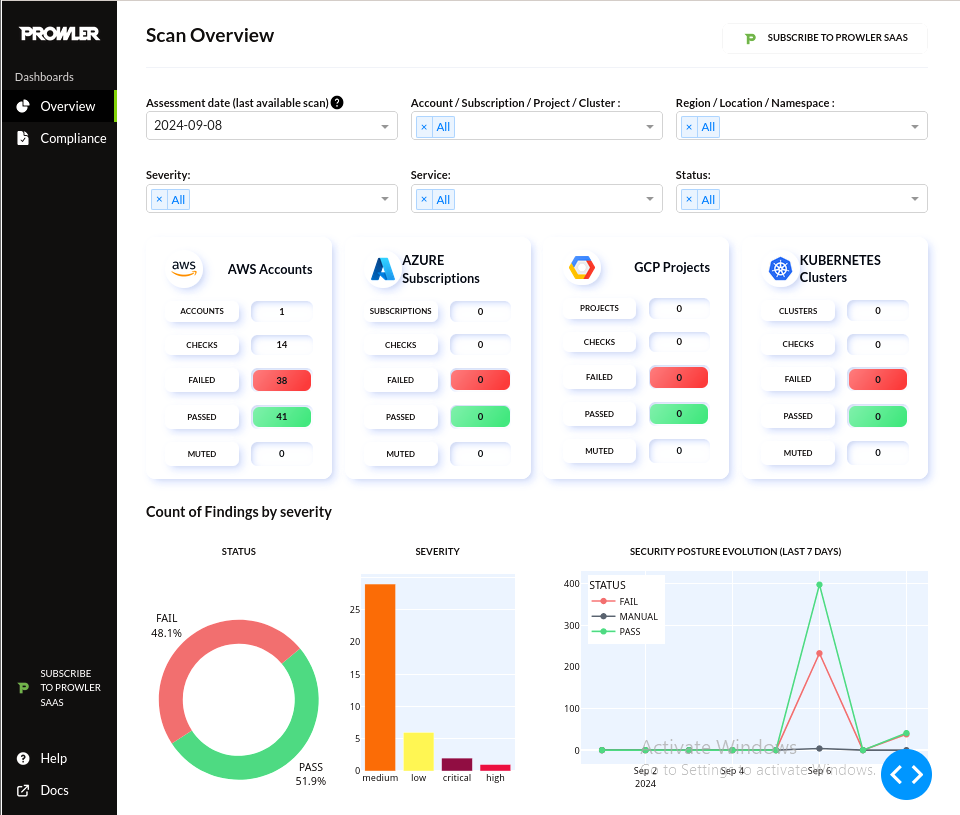
prowler dashboard
Explanation: The dashboard makes it easier to manage security assessments, especially in larger, multi-cloud environments where manual CLI operations would be more complex and harder to track.
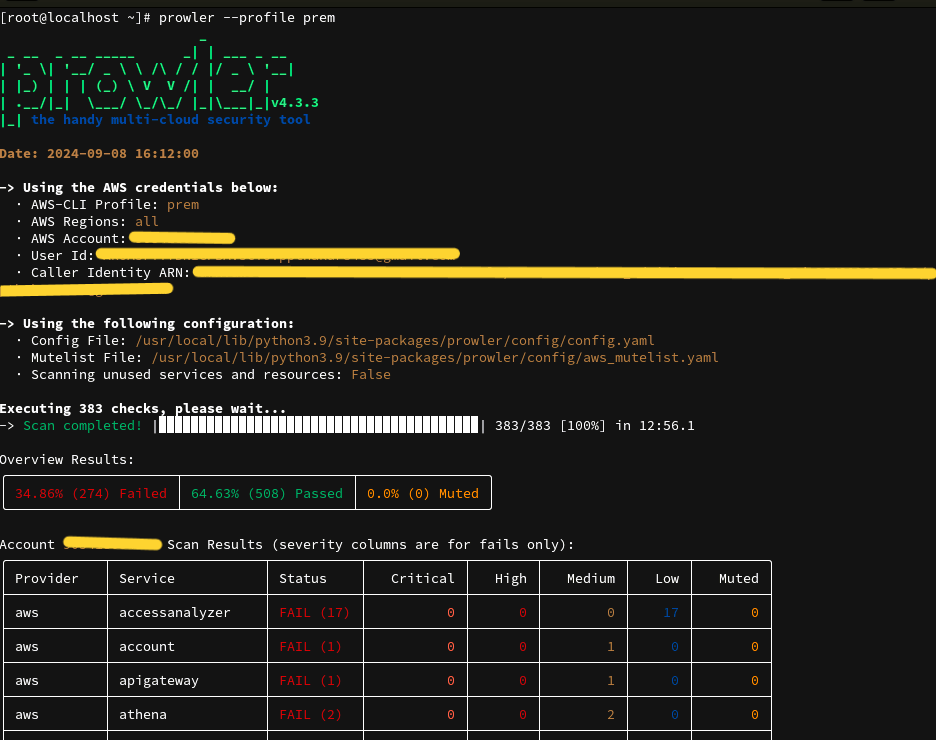
- Run Prowler with a Specific AWS Profile:
prowler --profile myawsprofile
Explanation: If you manage multiple AWS accounts, you can use a specific AWS profile to run the checks by using the --profile option. This is useful when you want to target a specific account.
Create a Custom Check
You can add custom checks to Prowler to meet specific security needs. Here’s an example of creating a custom check to identify IAM users who haven't logged in for 90 days.
Steps to Add a Custom Check:
- Run a Full Security Check for AWS:
Create a New Shell Script for Your Custom Check: Let’s say you want to create a custom check to ensure that all IAM users who have not logged in for the past 90 days. Create a new shell script for the check:
bash:
touch Unuse_IAM_Users.sh
chmod +x Unuse_IAM_Users.sh
- Add the Following Code:
#!/bin/bash
check_unused_iam_users() {
echo "Checking for unused IAM users (inactive for 90 days)..."
aws iam list-users --query 'Users[*].UserName' --output text | while read username; do
last_used=$(aws iam get-user --user-name "$username" --query 'User.PasswordLastUsed' --output text 2>/dev/null)
if [ "$last_used" == "None" ] || [ -z "$last_used" ]; then
echo "PASS: $username has never logged in."
else
days_since_last_used=$(($(($(date +%s) - $(date -d "$last_used" +%s))) / 86400))
if [ $days_since_last_used -ge 90 ]; then
echo "FAIL: $username has not logged in for $days_since_last_used days."
else
echo "PASS: $username is active."
fi
fi
done- Execute the Script:
bash:
bash Unuse_IAM_Users.sh
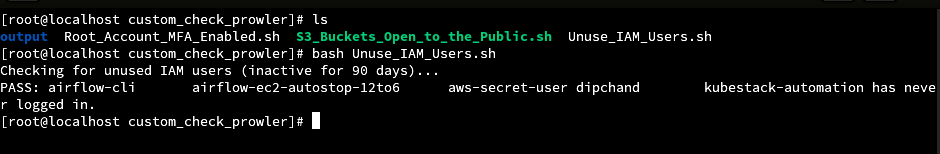
This check helps identify IAM users who haven’t logged in for 90 days and are potentially a security risk.
How Prowler is different from AWS Config
Here's a detailed comparison between Prowler and AWS Config, highlighting their key differences:
Feature | Prowler | AWS Config |
|---|---|---|
Purpose | Security auditing and compliance | Continuous monitoring and resource management |
Scope | Multi-cloud (AWS, Azure, GCP, Kubernetes) | AWS-specific resources |
Type of Checks | On-demand security assessments | Continuous compliance and configuration tracking |
Customization | Highly customizable with custom checks | Custom rules can be defined for AWS resources |
Usage | Command-line tool for audits and reporting | Service integrated into AWS Management Console |
User Interface | Primarily CLI with optional SaaS dashboard | Web-based dashboard in AWS Management Console |
Compliance Standards | Supports various standards like CIS, NIST, GDPR | Supports compliance against AWS best practices |
Frequency | Manual or scheduled runs | Continuous monitoring of resource states |
Reporting | Generates reports in multiple formats (CSV, JSON, HTML) | Provides configuration history and compliance status |
Summary of Differences:
- Prowler is designed for proactive security assessments across multiple cloud environments, providing flexibility in auditing security controls and ensuring compliance with various standards.
- AWS Config is focused on continuous tracking of resource configurations within AWS, ensuring that resources comply with desired configurations and helping to manage changes over time.
Overall, Prowler is ideal for security-focused teams needing to assess their cloud infrastructure actively, while AWS Config is suited for teams looking to maintain continuous compliance and configuration management within AWS.
Conclusion
Prowler is a powerful tool for anyone managing cloud environments and looking to ensure their security posture is top-notch. With its broad range of checks and user-friendly setup, it makes security assessments straightforward and effective. Whether you're using it for regular audits or as part of your continuous monitoring strategy, Prowler helps you stay on top of your security game and keep your cloud infrastructure safe.
For more details, check out the Prowler documentation and start making your cloud environments more secure today!
Checkout our article on setting up your own NAT Server and save on costs!
https://www.kubeblogs.com/use-your-own-nat-server-to-save-upto-40-month/

